In a new study, researchers from the University of Tokyo, Harvard University and the International Neurointelligence Research Center have revealed a technique to create realistic robotic skin using living human cells. As a proof of concept, the team designed a small robotic face capable of smiling, completely covered in a layer of pink living tissue.
The researchers note that using living skin tissue as a robot shell has benefits, as it is flexible enough to transmit emotions and can potentially repair itself. “As the role of robots continues to evolve, materials used to cover social robots must exhibit realistic functions, such as self-healing,” the study’s researchers wrote.
Shoji Takeuchi, Michio Kawai, Minghao Nie, and Haruka Oda are the authors of the study, titled “Skin ligament-inspired perforation-type anchors for robotic face covered with living skin,” which will be published in July in Cell Reports Physical Science. We learned about the study via a report published earlier this week by New Scientist.
The study describes a novel method for attaching cultured skin to robotic surfaces using “drill-type anchors” inspired by natural skin ligaments. These small V-shaped cavities in the robot’s structure allow living tissue to infiltrate and create a secure bond, mimicking how human skin adheres to underlying tissues.
To demonstrate the skin’s capabilities, the team designed a palm-sized robotic face capable of forming a convincing smile. Actuators connected to the base allowed the face to move and the living skin to flex. The researchers also covered a 3D-printed static head form with the designed skin.
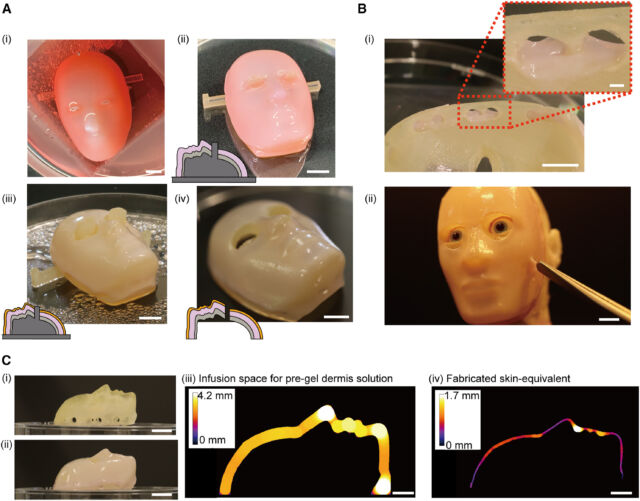
Takeuchi et al. created their robotic face by 3D printing a resin base with the drilled anchors built into it. They then applied a mixture of human skin cells onto a collagen scaffold, allowing living tissue to grow inside the anchors.
